2. Introduction
Solid is a specification [solid-protocol] for decentralised personal data stores (called `Pods') that uses linked data and Web standards to achieve user control and interoperability. The access to data stored within Solid Pods is governed by the Web Access Control (WAC) specification [wac] which uses IRIs to represent resources and agents, and stores authorisation statements within Access Control Lists (ACL) defined per resource or inherited from the parent resource. Therefore, in Solid, the user controlling the ACL is the entity responsible for deciding who has access to the data.
Given that Solid provides a way for personal data to be stored and managed by individuals, it is important to consider the impact and application of data protection and privacy laws such as the European General Data Protection Regulation (GDPR) that define specific concepts and obligations for how personal data can be collected, stored, used, and shared. In addition, such laws also specify various rights and the legal basis used to justify using the data and the conditions for their validity. In particular, GDPR's Articles 13 and 14 require controllers to provide information such as identity, purpose, personal data categories, legal basis, and recipients where they collect personal data directly or indirectly from individuals.
Applied to Solid, this information can be presented using conventional methods, such as a notice provided on the data requester's website, and the resulting authorisation decision made by the individual stored within the ACL. However, for individuals to control their data practices, the Solid Pod must contain this information as well so that the individual has the opportunity to:
(i) inspect their personal data within an environment under their control;
(ii) store it for accountability purposes;
(iii) determine their data sharing preferences; and
(iv) be assisted in expressing and enforcing their data sharing preferences.
To achieve these goals, the following requirements motivate our approach to extend Solid’s existing ACL mechanism using the ODRL Vocabulary and Expression specification to define ‘sticky policies’ that express permissions and / or prohibitions associated with data stored in a Solid Pod and utilises DPV as a controlled vocabulary for invoking privacy and data protection-specific terms.
R1. Support specifying user preferences as policies.
R2. Incorporate vocabulary specifying or aligned to legal concepts.
R3. Support specifying permissions and prohibitions at arbitrary granularity.
R4. Support identifying and resolving conflicts based on scope.
R5. Record (store) policies used to authorise access.
R6. Support querying policies and authorisations for introspection of data use.
2.1 Ontology Requirement Specification Document
| ODRL Profile for Access Control in Solid | |
|---|---|
| 1. Purpose | |
| The purpose of this profile of ODRL is to support policies determining the access control to personal data stored in Solid Pods. | |
| 2. Scope | |
| The scope of this profile is limited to the definition of an ODRL Profile for Access Control in Solid. In particular, the introduced elements will serve one of these purposes: (i) define actions supporting enforcement of current ACL verbs, (ii) define data protection-related actions and restrictions defined in GDPR, (iii) any vocabulary element to support policy patterns that can be anticipated to be common, and (iv) elements necessary to support the authorization reasoning decision. | |
| 3. Implementation Language | |
| OWL | |
| 4. Intended End-Users | |
| Developers of Solid servers and Solid clients. | |
| 5. Intended Uses | |
|
Use 1. Declaration of a policy by an individual storing personal data in a Pod. Use 2. Request of data made by a person or application to gain access to the data in different modalities. Use 3. Contextual elements to be considered in the authorization decision. Use 4. Explanation of the authorization decision. |
|
| 6. Ontology Requirements | |
| a. Non-Functional Requirements | |
| NFR 1. The ontology shall be published online with standard documentation. | |
| b. Functional Requirements: Groups of Competency Question | |
| CQG1. Related to authorization | CQG2. Related to GDPR |
|
CQ1. Which actions are to be authorized? CQ2. Which requirements are to be authorized? CQ3. Who are the parties intervening in policy? CQ4. Which is the priority of a certain policy? CQ5. Which are the contextual elements to be considered in the authorization decision? |
CQ6. Which obligations and requirements, and information about personal data and its processing are necessary? CQ7. Which is the legal identification of the policy parties? |
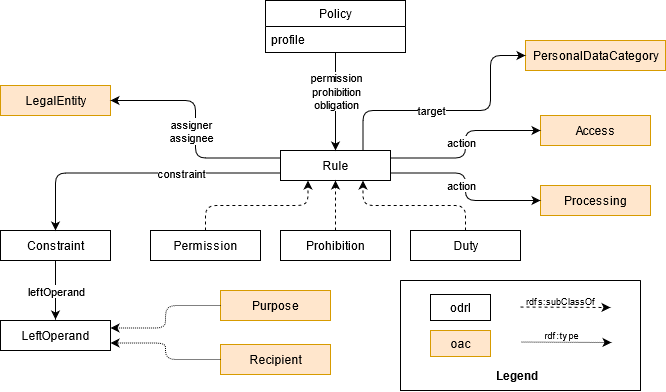
2.2 Profile diagram
The concepts specified by the ODRL Profile for Access Control in Solid are shown in the figure below.
2.3 Document Conventions
| Prefix | Namespace | Description |
|---|---|---|
| odrl | http://www.w3.org/ns/odrl/2/ | [odrl-vocab] [odrl-model] |
| rdf | http://www.w3.org/1999/02/22-rdf-syntax-ns# | [rdf11-concepts] |
| rdfs | http://www.w3.org/2000/01/rdf-schema# | [rdf-schema] |
| owl | http://www.w3.org/2002/07/owl# | [owl2-overview] |
| dct | http://purl.org/dc/terms/ | [dct] |
| ns1 | http://purl.org/vocab/vann/ | [ns1] |
| xsd | http://www.w3.org/2001/XMLSchema# | [xsd] |
| skos | http://www.w3.org/2004/02/skos/core# | [skos] |
| cert | http://www.w3.org/ns/auth/cert# | [cert] |
| dpv | http://www.w3.org/ns/dpv# | [dpv] |
| acl | http://www.w3.org/ns/auth/acl# | [acl] |
| oac | https://w3id.org/oac/ | [oac] |